Laravel SMTP Crack: Unveiling the Vulnerability with Laravel SMTP Checker by XCATZE
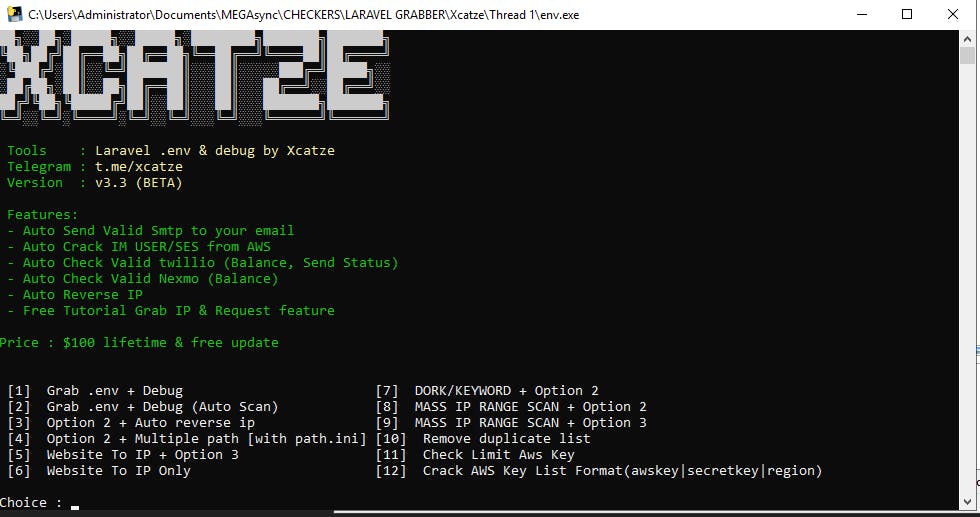
I got the feeling that it works on non-SSL web apps, with just IP or unsecured domain names, and also when APP_DEBUG=true on dev or staging. Debug should be disabled in production.
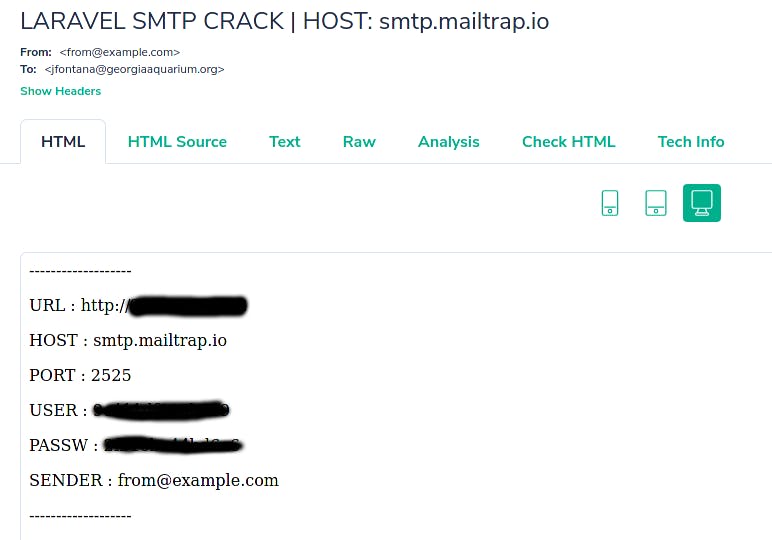
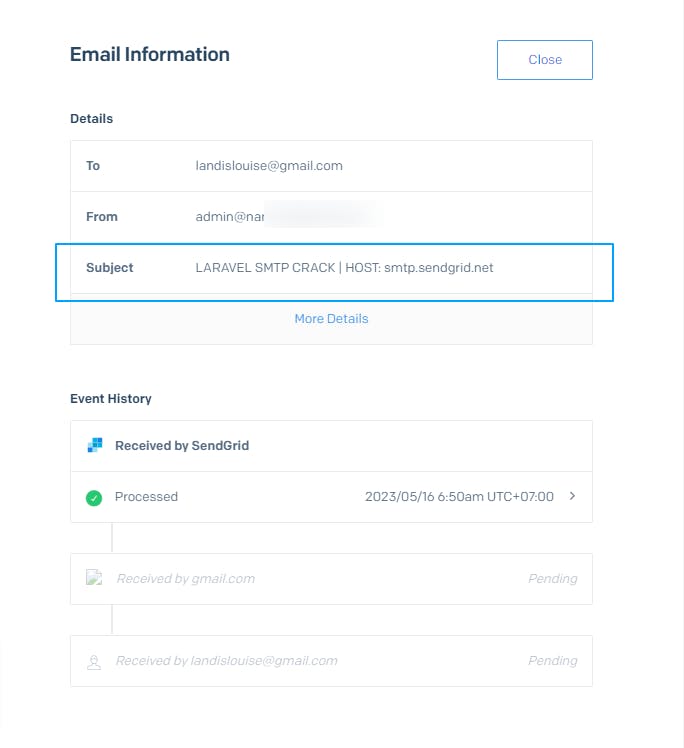
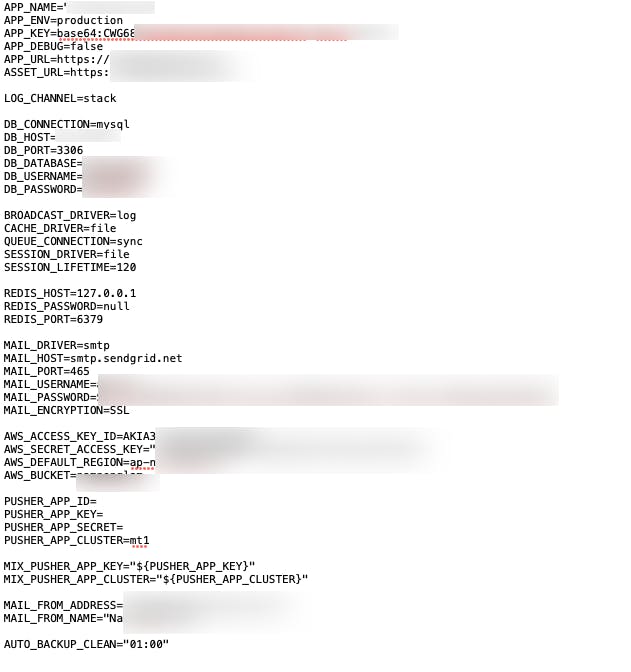
Spammers have one goal, to send as much spam as cheaply as possible with good IPs that are not blocked, and we've been hearing more and more reports of Laravel apps getting their SMTP credentials hacked and then the attackers using those to send junk.
This is not related to any vulnerability in Laravel itself. The issue is coming from improper server setups or not turning off debug mode.Hide your .env file
Laravel ships with a .env file that holds many configuration variables, including your database information and your mail server details; if this file becomes web-accessible, anyone can get your sensitive data and use those credentials.
By default, the directory structure of a default Laravel app has a public folder and that and only that should web-accessible.
In most situations, following the documentation on deployments section will set this up probably for you.
Feedback from Laravel
I'm sorry to hear about the issue you're facing. It seems that you received notifications about your SMTP credentials being used to send unauthorized emails, and upon checking the logs, you found that these emails were sent using your SMTP information. You first investigated your application's source code but didn't find any issues, as you manage your source code using Git. After further research, you discovered that this is a new vulnerability in Laravel. You attempted to hide the .env file, but it was not successful, and your SMTP credentials continue to be abused. When you sought assistance from Sendgrid technicians, they informed you that you were being attacked from the IP address: xx.xxx.xx/.env. Although you had previously blocked the domain/.env, it appears to be a severe vulnerability.
It is indeed concerning that despite your efforts to secure your application and hide the .env file, attackers are still able to exploit the vulnerability and gain access to your SMTP credentials. In situations like this, it's essential to take immediate action to mitigate the issue and prevent further unauthorized use of your SMTP server.
Here are some steps you can consider taking:
Change SMTP credentials: Start by changing your SMTP credentials to prevent any further unauthorized access. Update the credentials in your application's .env file and ensure they are strong and secure.
Update Laravel and dependencies: Make sure you are using the latest version of Laravel and all its dependencies. Developers often release security patches and fixes for known vulnerabilities, so keeping your framework and packages up to date is essential.
Review server and application security: Conduct a thorough review of your server and application security. Check for any other potential vulnerabilities, such as exposed sensitive files or misconfigured permissions. Ensure that you follow best practices for server configuration and application hardening.
Implement additional security measures: Consider implementing additional security measures to protect your application. This may include enabling firewalls, implementing intrusion detection systems, and using tools like fail2ban to block suspicious IP addresses.
Monitor server logs: Continuously monitor your server logs to detect any suspicious activities or unauthorized access attempts. This will help you identify and respond to potential attacks promptly.
Engage a security professional: If the issue persists or if you require further assistance, it's advisable to consult a security professional who specializes in web application security. They can perform a comprehensive security audit and provide recommendations specific to your application.
Remember, maintaining the security of your Laravel application is an ongoing process. Regular updates, proactive security measures, and vigilance are crucial to mitigate risks and protect your sensitive information.
To hide the .env file on Nginx and Apache servers, you can follow the steps below:
- Nginx:
Open the Nginx configuration file for your application (usually located in the
/etc/nginx/sites-available/directory).Locate the
serverblock for your domain or IP address of your Laravel application.Add the following code inside the
serverblock:location ~ /\.env { deny all; }Save and close the configuration file.
Restart Nginx to apply the changes.
- Apache:
Open the Apache configuration file for your application (usually located in the
/etc/apache2/sites-available/directory).Locate the
<VirtualHost>block for your domain or IP address of your Laravel application.Add the following code inside the
<VirtualHost>block:<FilesMatch "^\.env$"> Order allow,deny Deny from all </FilesMatch>Save and close the configuration file.
Restart Apache to apply the changes.
After performing the above steps, the .env file will be hidden and inaccessible from the outside through a web browser. This helps protect sensitive information in the .env file from being exposed or misused.
Please note that hiding the .env file is just an additional layer of protection and does not substitute for ensuring the overall security and safety of your Laravel application. You should also consider other security measures such as keeping Laravel up to date, using strong passwords, and performing regular security checks to ensure the safety of your application.
I researched the sources: Laravel News, Serverfault, Reddit, Stack Overflow, .etc
